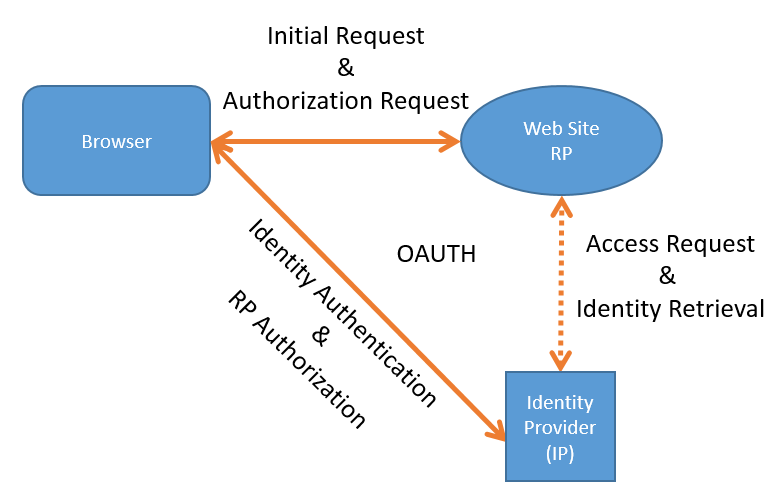
So what is this OAuth? This is what wikipedia says:
OAuth is an open standard for authorization, commonly used as a way for Internet users to authorize websites or applications to access their information on other websites but without giving them the passwords.[1] This mechanism is used by companies such as Google, Facebook, Microsoft and Twitter to permit the users to share information about their accounts with third party applications or websites.
So let me start off by saying I am not sure what the difference between OAuth 1.0 and 2.0 is and i’ll be skipping ahead directly to OAuth 2.0.
Right, so first I read up about OAuth and I find this interesting gossip section about this wizard “Eran Hammer” that created OAuth 1.0 and got upset!, then threw his toys around and stormed off when OAuth 2.0 came out because corporates broke his standard to suit their own needs. Jip the web is not really free – is it! Interesting topic! Mental note, check out his Oz and Hawk projects. I wonder how widely that is being used?
I continued to read about OAuth and I notice that OAuth is not really about user authentication, instead it seems more about application authorization and integration! Application X & Y is allowed to access application Z. Next thing I notice is that OAuth uses http, this tells me its build for the web and not for back office systems. Probably mainly for website to website access-control, I wonder if there is provision for desktop applications?
The reason I am looking at this is to see how I can integrate a WS-Federated STS and chain it, to use OAuth as an IP-STS. This will allow users to decide, no I want to log-in using my facebook, gmail or twitter account instead of a Active Directory account. I am going to start reading about the integration with twitter as it seem that most c# examples deal with them.
Seeing as I am new to this topic I will probably get it wrong a few times but from what I can see.
- The consuming application enrollees itself with the OAuth Provider like facebook, twitter, gmail. You get a special unique key for our application!
- Next, when a users wants to sign-in to the OAuth provider we do a “request” and supply our unique application key. We get back a OAuth request token – another key!
- Now I call the provider’s website in a new browser window and supply the request token.
- The provider’s website allows the user to authenticate and provides him with a pin that he then needs to enter into the calling application. I don’t like this – feels messy. a) This is obviously meant to be a synchronize process cause the response from a request is the next request’s input – but now we opening a browser window in between – where do I go with the state? b) Why is this pin not returned automatically to the calling app via redirect? I assume he only needs to this once for authorization. Wonder does all OAuth providers use this pin?..lets continue reading.
- We pass the pin back to the provider and received an OAuth access token.
- Next we use the OAuth access token to create a signed a header and from this point on we can do various requests to retrieve information regarding the Identity of the user.
Right, at this point in time it’s all just theory and I need to go and put this into practice by doing a sample or something. As I work in C#, i guess ill have to role my own API for this. I briefly looked online and it was not a pretty sight. Will let you know what I do later.
Cheers.