I created a windows forms application sample that can assist with decoding to FedAuth tokens captured from tools like Fiddler, source is included. It is downloadable from this link.
The sample and example below will work for all WS-Federated responses as long as it does not contain reference tokens.
Extract the federated response
Start of by using your web browser and recording the sign – in request and responses using Fiddler.
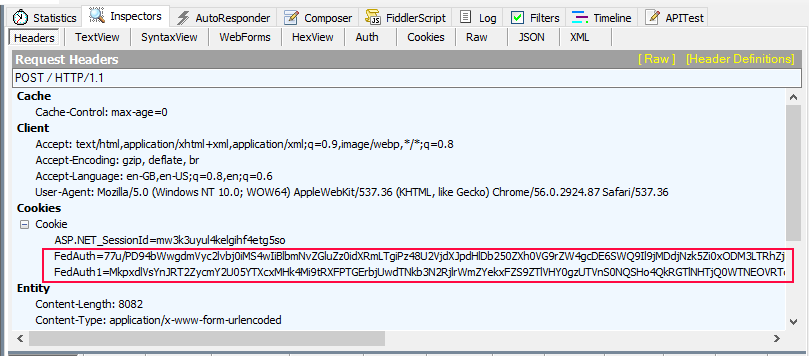
The response you need to look for is the first response from the Identity Provider (STS) to your application. Once the RP has received the response it will turn the response into FedAuth cookies. The name of the cookies can be different so its best to look for something with similar content.
If a ChunkedCookieHandler is used the token will be broken up into multiple FedAuth cookies. The cookies will look like it is encrypted but in fact they are all simply Base64 encoded.
Copy the contents of each of the FedAuth cookies and paste them in order in notepad with no spaces or carriage return between them.
Ensure you have the certificate
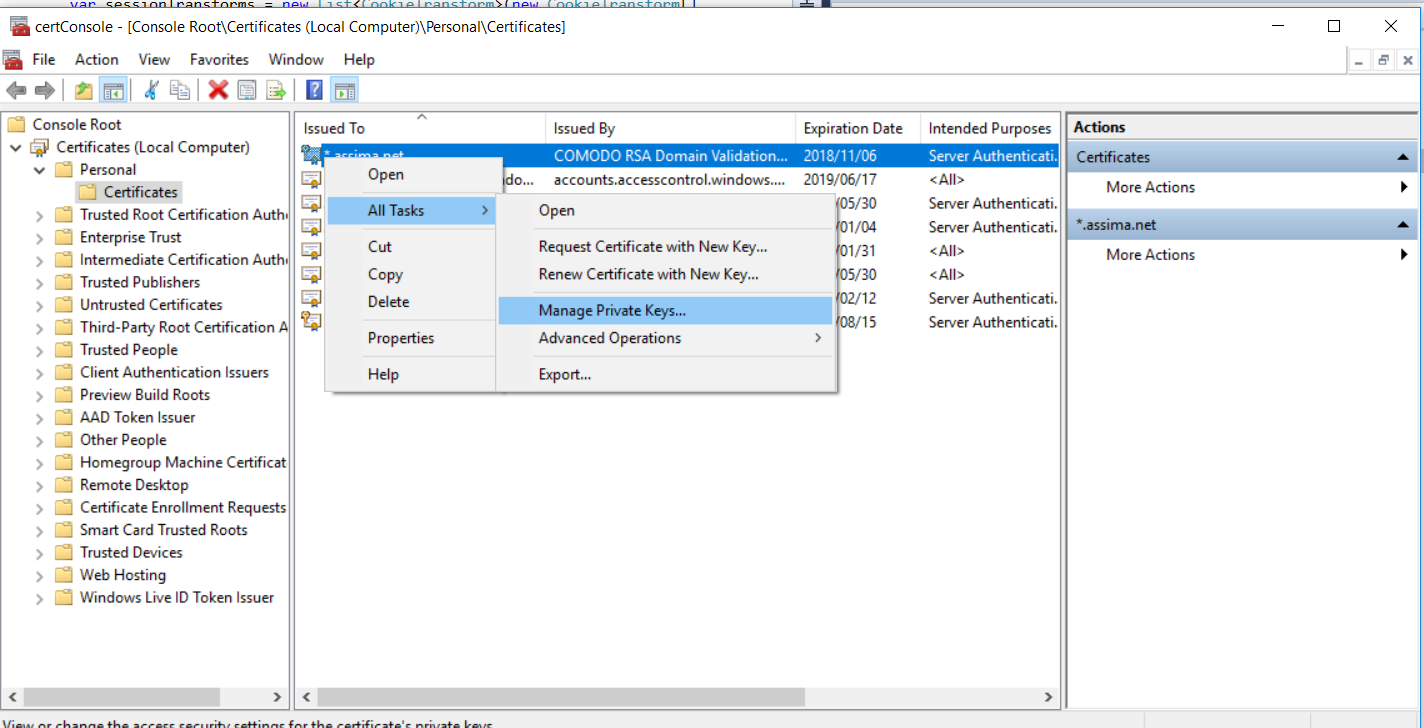
Make sure your user under which the application runs has access to the private key of the certificate. You can check this via MMC.
The certificate you use can be identified by the Identity provider metadata file. The Identity provider has an url to the metadata that usually looks something like this. https://sts.com/adfs/ls” The xml will have a element for signature. Inside that element you will find a element called KeyInfo, this will contain a base64 certificate.
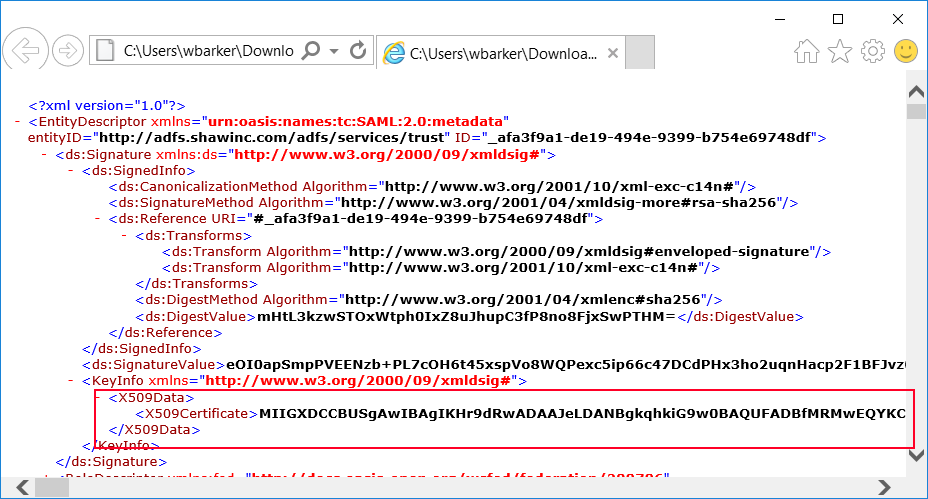
Copy the cert value out to notepad. Save the file to disk, rename its extension to *.cer and Import the file
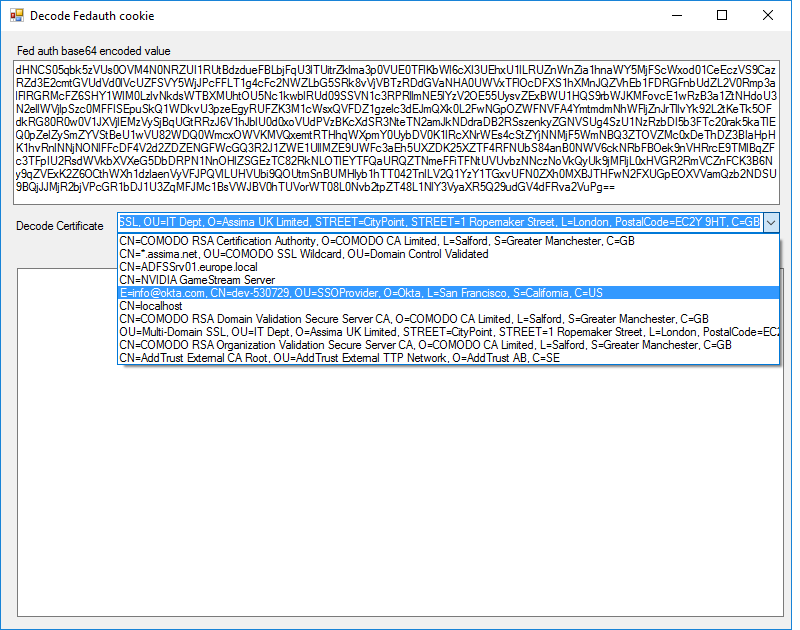
Decode the fedauth token
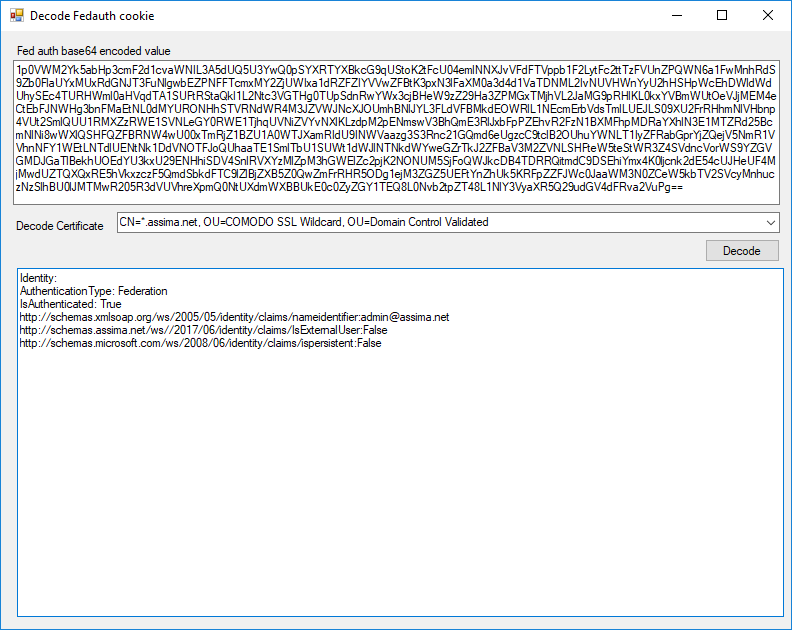
If you have retrieved the FedAuth token and made sure the certificate is the correct one then paste the Base64 string into the application I provided. Select the correct certificate and click decode.
It then prints out the Identity and claims that are provided within the SessionToken.
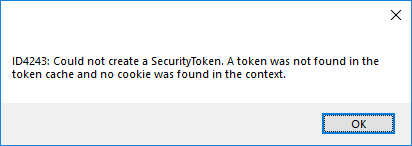
No Token found or unable to decode
If the application is unable to decode the token and gives the following error.
ID4243:Could not create a SecurityToken
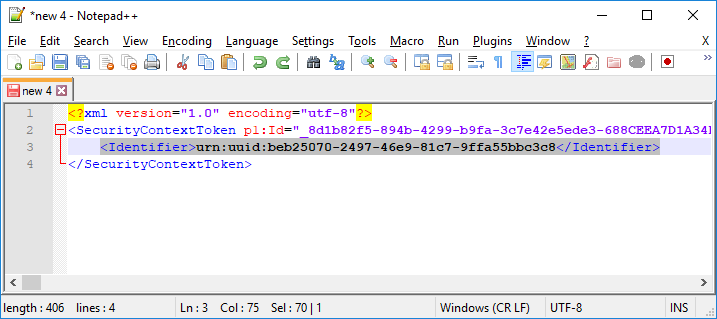
Then copy the FedAuth base64 string from your notepad to https://www.base64decode.org. If you decode the token and it contains an Identifier as in the xml below then the claims are stored on the server and not within the token.
This is a reference token. The token in this case only has a identifier to the token stored in the server side cache. Nothing can be done to get around this unless you know the http url to the token cache or have access.
Below is the key snippet of code that does the decoding of the token.
private SessionSecurityToken decodeToken(string decodedFedAuthCookieXml)
{
SessionAuthenticationModule m = new SessionAuthenticationModule();
m.FederationConfiguration = new System.IdentityModel.Services.Configuration.FederationConfiguration(false);
m.FederationConfiguration.ServiceCertificate = GetCertificate(cmbCertificates.SelectedItem.ToString());
m.FederationConfiguration.CookieHandler = new ChunkedCookieHandler();
// Specifies the certificate use to decrypt the federation token.
var sessionTransforms = new List(new CookieTransform[]
{
new DeflateCookieTransform(),
new RsaEncryptionCookieTransform(m.FederationConfiguration.ServiceCertificate),
new RsaSignatureCookieTransform(m.FederationConfiguration.ServiceCertificate)
});
var sessionHandler = new SessionSecurityTokenHandler(sessionTransforms.AsReadOnly());
m.FederationConfiguration.IdentityConfiguration.SecurityTokenHandlers.AddOrReplace(sessionHandler);
byte[] cookieBytes = Encoding.UTF8.GetBytes(decodedFedAuthCookieXml);
SessionSecurityToken token = m.ReadSessionTokenFromCookie(cookieBytes);
return token;
}
If the solution above does not help
Please tell me by posting in the comments and try one of the following so long.
- Update 2017/10/09 – Fixed a bug in the example. The application was trying to use DPAPI instead of RSA.
- Update 2017/11/16 – Fixed the broken link in the article.
- Update 2018/03/24 – There have been reports of people unable to decode their tokens. – I added some error handling to prevent crashes. Also adjusted the manifest file of the application to run at a the highest allowed execute level. The user must have manage rights to the private key of the certificate.
Your link to the source is broken. Thank you so much for this! Saved me a lot of time.
Thank you for letting me know. The link has been fixed. 🙂
Hi Wayne,
Unfortunately your link is still broken. Could you fix it please? That tool would be very useful to us.
Also, how do you know which certificate to use to decode the token?
Where can we find it?
thank you in advance.
tony.
Hi Tony, I have mailed you with attachment directly. For some reason it appears as if all my zip files have been removed from my blog although the references remain in the wordpress db. Sorry for the inconvenience.
Hi Wayne.
This looks great! I would also very much like to take a look at the sample application and code. If you could send it to me, I would be most grateful! Or maybe you could make it available through a shared link on Dropbox or Google Drive or similar?
@TonyM: The certificate to use for decryption would be the one that is configured as serviceCertificate under system.identityModel.services -> federationConfiguration in your application’s web.config file. See https://docs.microsoft.com/en-us/dotnet/framework/configure-apps/file-schema/windows-identity-foundation/servicecertificate
Hi, can you email me zip file also?
How do you know which cert to use? hmm. If you know the source of the token you should know which cert to use.
If you can know the metadata service address of the STS then you con find the cert in there. The url usually looks something like this. https://sts.com/adfs/ls” The xml will have a element for signature. Inside that element you will find a element called KeyInfo, this will contain a base64 certificate.
Copy the cert value out to notepad. Save the file to disk, rename its extension to *.cer and Import the file. Now you can decode the fedauth token with the certificate provided by the STS.
so this is great information and the project you posted does not work.