Recently I had to do a implementation of SAML2 within .Net, .Net does not have any native support for SAML2 and as a result I had to approach a 3rd party provider called Component Space. Their support is really first class.
 I was working with WIF in .Net with WS-federation which made use of the .Net authentication pipeline. Unfortunately the Component Space SAML2 component did not plug into this pipeline and this was a requirement of mine. I had to support both WS-federation and SAML2. So I set out to develop a module that would allow me to use the SAML2 component with the .Net authentication pipeline.
I was working with WIF in .Net with WS-federation which made use of the .Net authentication pipeline. Unfortunately the Component Space SAML2 component did not plug into this pipeline and this was a requirement of mine. I had to support both WS-federation and SAML2. So I set out to develop a module that would allow me to use the SAML2 component with the .Net authentication pipeline.
The SAML2 module can be downloaded here but please note that you still need to purchase the Component Space SAML2 component for it to function. I will attempt to assist those that wish to use it but there is no guarantee and no future maintenance.
The module I developed had to support;
- Configuration by means of the web.config file.
- Had to plug into the .Net Authentication pipeline.
- Support Sign out requests
- Metadata requests for integration
As a result of these requirements I was forced to use the low level API of component space for most of the module, the only exception being that of the metadata. To make the module able to recognize when metadata, sign in assertion and sign out request was initiated I had to define some constants and the module ended up being driven by means of parameters.
- Metadata request: HTTP:\\company.com?inst=metadata
- Sign in request: HTTP:\\company.com?inst=signIn
- Sign out request: HTTP:\\company.com?inst=signOut
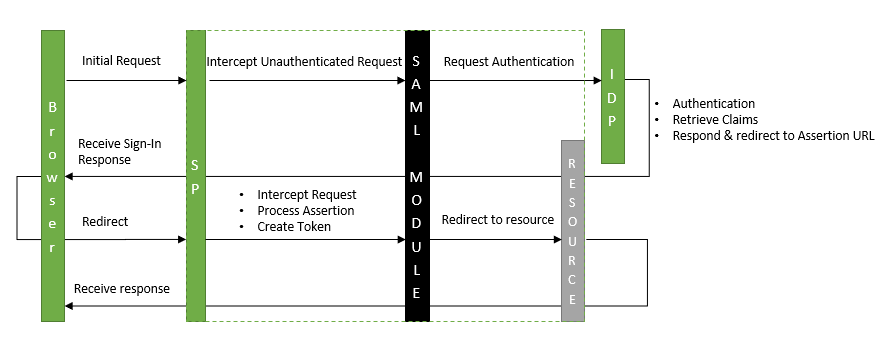
Below is a visual representation of a sign in request to give you an idea on how this would function.
Configuring the module.
The following changes need to be made to the web.config file of your application.
Below you can see how I switch between WS-Federation and SAML2.
<modules runAllManagedModulesForAllRequests="true"><add name="AuthenticationModule" type="System.IdentityModel.Services.SessionAuthenticationModule" preCondition="managedHandler" /><!-- SAML2 Module --><br /><add name="AuthenticationModule" type="Company.Security.SAML2Module.SAML2AuthenticationModule, Company.Security.SAML2Module" preCondition="managedHandler" /><!-- WS-Federation Module --><!-- <add name="WSFederationAuthenticationModule" type="System.IdentityModel.Services.WSFederationAuthenticationModule, System.IdentityModel.Services, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089" preCondition="managedHandler" />--></modules>
Setup the component space config for the metadata. This is the SAML.config file as per the component space documentation.
<?xml version="1.0"?><SAMLConfiguration xmlns="urn:componentspace:SAML:2.0:configuration"><ServiceProvider Name="https://SpDomain" Description="SP" AssertionConsumerServiceUrl="~Inst=SignIn" LocalCertificateSerialNumber ="123"/><PartnerIdentityProviders><!-- ADFS --><PartnerIdentityProvider Name="https://saml.domain/adfs/ls/" Description="ADFS" SignAuthnRequest="true" SignLogoutRequest="true" WantAssertionEncrypted="false" WantLogoutResponseSigned="true" SingleSignOnServiceBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" SingleSignOnServiceUrl="https://saml.domain/adfs/ls/" SingleLogoutServiceUrl="https://saml.domain/adfs/ls/" PartnerCertificateSerialNumber="456"/> <PartnerIdentityProvider Name="https://saml.domain/adfs/services/trust" Description="ADFS" SignAuthnRequest="true" SignLogoutRequest="true" WantAssertionEncrypted="false" WantLogoutResponseSigned="true" SingleSignOnServiceBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" SingleSignOnServiceUrl="https://saml2.domain/adfs/ls/" SingleLogoutServiceUrl="https://saml2.domain/adfs/ls/" PartnerCertificateSerialNumber="456"/> </PartnerIdentityProviders> </SAMLConfiguration>
The following app settings need to be added.
<!-- SAML2 Settings. --><br /><add key="IdpUrl" value="https://adfssrv.domain/adfs/ls/" /><add key="IdpCertificateSerialNumber" value="123" /><add key="SpCertificateSerialNumber" value="456" /><add key="SpCertificateDigestMethod" value="http://www.w3.org/2001/04/xmlenc#sha256" /><add key="SpCertificateSignatureMethods" value="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256" /><add key="RedirectUriOnSignOut" value="https://domain/SignoutPage"/><add key="SignAuthnRequest" value="false" /><add key="SignLogoutRequest" value="true" /><add key="IsPassive" value="false" /><add key="ForceAuthen" value="false" />
Feel free to use the module and drop me some feedback.
Related
Integrate Ws-Federation into Asp.Net Core
Integrate Ws-Federation into Asp.Net
Pingback: Integrate Ws-Federation into Asp.Net Core - Wayne Clifford Barker
Pingback: Passive STS integration
Pingback: Integrate Ws-Federation into Asp.Net